
Case Study: JACKAL
Notional provides extensive security audits for chain teams and has built a reputation in the Cosmos ecosystem for its ability to spot and call out security flaws. A recent example of this was when Jacob Gadikian reviewed the codebase for Jackal and found several potentially insecure aspects to the project's codebase. The Jackal team responded quickly and invited Jacob to provide a detailed security audit.
During an investigation conducted by Jacob, several potential issues were outlined. These included a determination of whether validator filesystems were put at risk, an assessment of the level of interplay between the random HTTP server and filetree and storage, and an examination of whether user data or funds were put at risk and to what degree. According to Jacob's findings, validator filesystems were not at risk, but the modules require refactoring before being put back into play.
User data or funds were not put at risk, except in the case of an adversarial economic attack scenario where an adversary attempts to drain liquidity from exchanges where JKL is listed by halting JKL. Jacob also investigated IBC transactions between Jackal and Osmosis and history from the Secret Network. Community feedback was mixed, mostly airdrop related. The Jackal team chose to build their own solution rather than use Secret.
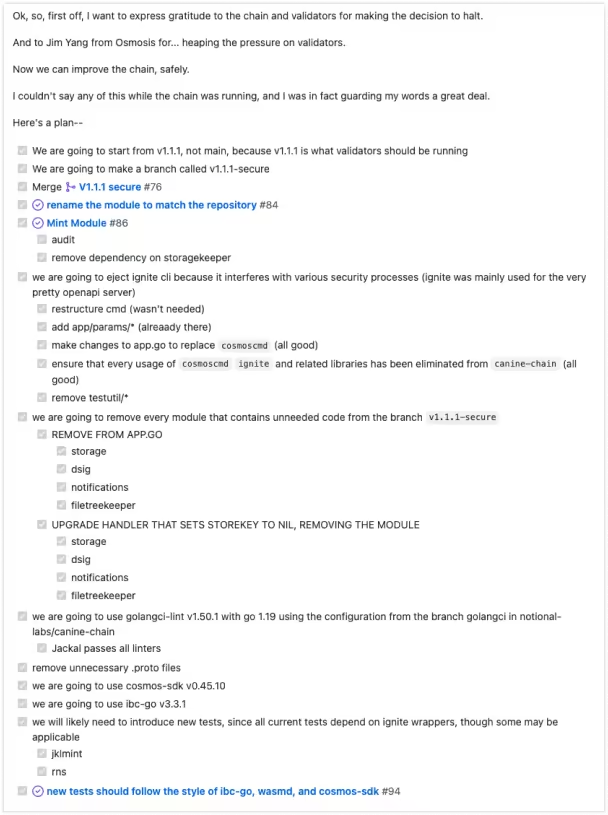
This decision requires Notional's team to always have someone on call to respond to questions and emergencies with the STRIDE team. To meet this requirement, Notional aims for a 5-minute response time for customer questions. As a result of the investigation, several modules were removed from the Jackal codebase, and new code was added to ensure that it is more secure going forward. Further action items to assess Jackal include support for IAVL, authz integration, chain upgrade to v4, auditing of pull requests, and Dragonberry patching. A summary of the findings and actions taken by the Jackal team can be found on their official Medium page.
User data or funds were not put at risk, except in the case of an adversarial economic attack scenario where an adversary attempts to drain liquidity from exchanges where JKL is listed by halting JKL. Jacob also investigated IBC transactions between Jackal and Osmosis and history from the Secret Network. Community feedback was mixed, mostly airdrop related. The Jackal team chose to build their own solution rather than use Secret.

This decision requires Notional's team to always have someone on call to respond to questions and emergencies with the STRIDE team. To meet this requirement, Notional aims for a 5-minute response time for customer questions. As a result of the investigation, several modules were removed from the Jackal codebase, and new code was added to ensure that it is more secure going forward. Further action items to assess Jackal include support for IAVL, authz integration, chain upgrade to v4, auditing of pull requests, and Dragonberry patching. A summary of the findings and actions taken by the Jackal team can be found on their official Medium page.




